
For Mortgage and Real Estate Professionals Only
LAUNCH TOP PERFORMING MORTGAGE & REAL ESTATE ADS IN LESS THAN 3 CLICKS
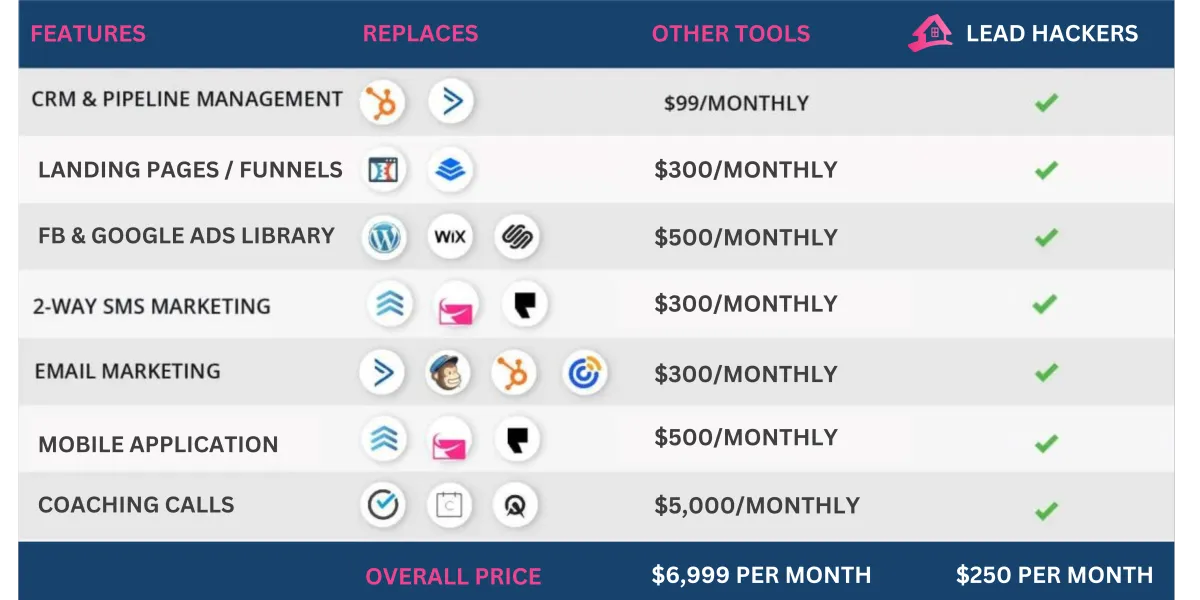
This is the first true All-in-One CRM with Lead Generation Capabilities. ZERO experience required.
First All in One CRM Solution With Lead Generation Capabilities
Equipped With Proven Ads Library

How It Works
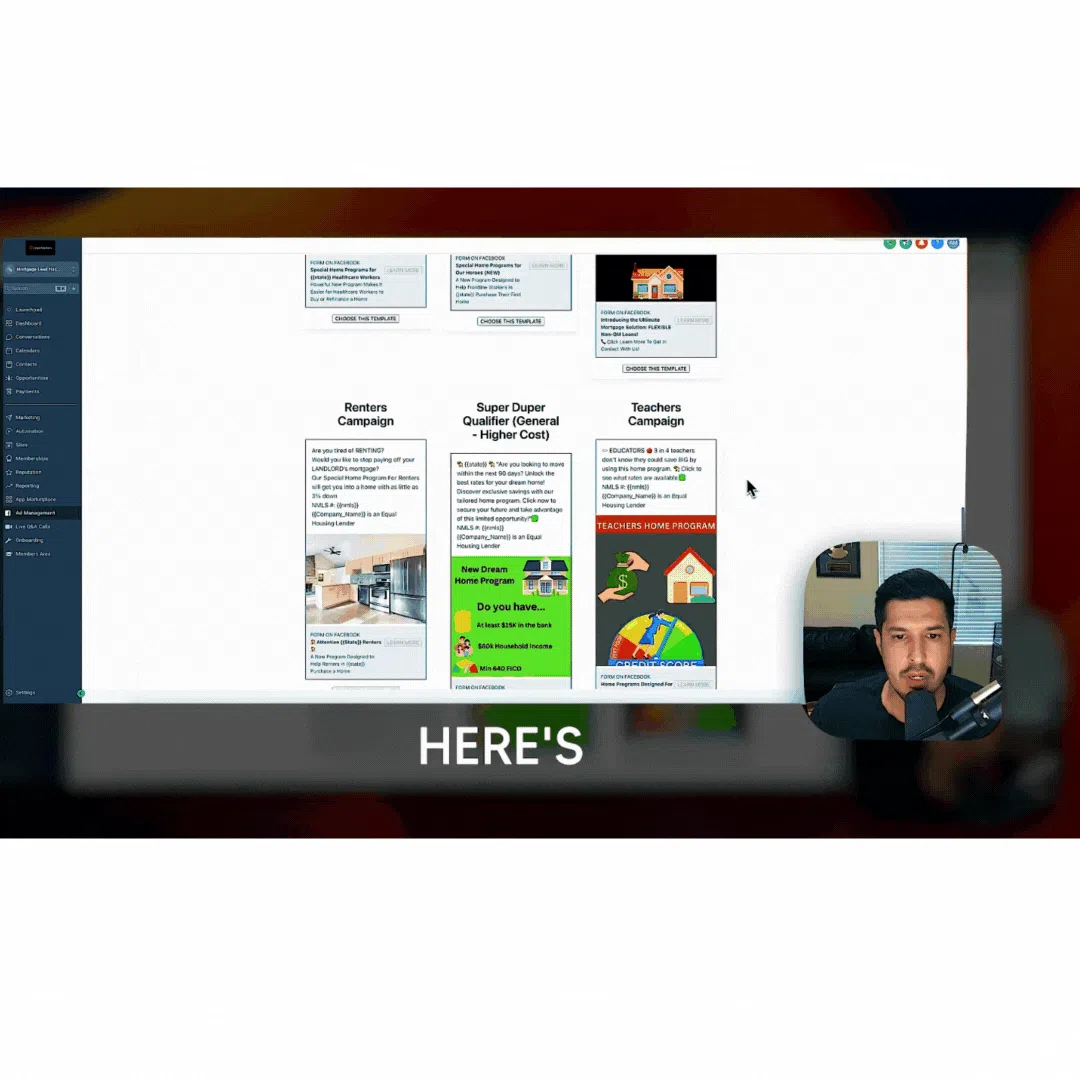
Ads Launcher
Launch your own Facebook & Instagram Ads with zero prior experience! Choose a pre-built, proven mortgage or real estate ad
from our library and start receiving leads in as little as 24 hours.
Landing Pages
We provide you with a pre-built landing page/funnel that will book you appointments with high intent leads on autopilot. This landing page has a survey on it that extracts critical information such as estimated credit score, annual household income, and many other attributes of your lead.

Automated SMS Follow Up
Every single leads will be texted within minutes of them filling out a form, ensuring speed to lead at the highest level. The automation will initiate conversations for you to pick up, right where they left off.
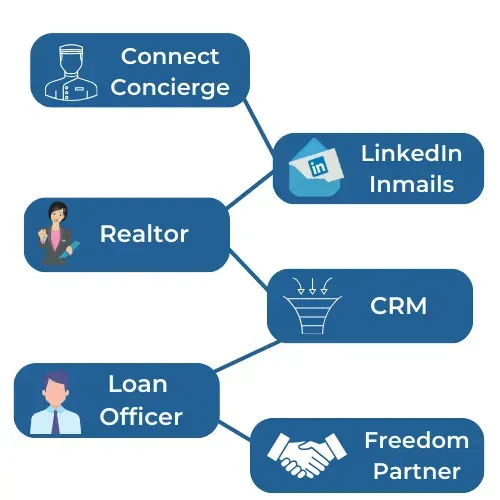
Automated Email Follow Up
Your leads will automatically be dropped into an email drip campaign. All emails are value driven emails that educate your potential buyer on both mortgage and real estate. These emails contain beautiful imagery and a call to action equipped with a link to your calendar so your leads can directly book appointments.
Coaching Calls
Each Lead Hacker gets FREE coaching calls multiple times per week on how to use the software, ad strategies, dialing strategies, targeting strategies, sales scripts, and much more.
Lead Hacker CEO Alex Machuca's Keynote Speech At The LOSummit 2023
Frequently Asked Questions
Is there a contract?
Our service operates without any binding contracts, providing flexibility and freedom to our users.
How Much Should I Spend On Ads?
Our official recommendation is $35 per day for peak optimization. However, many Lead Hackers get away with spending as little as $20 per day. At the end of the day your ad budget is in your complete control, these are simply our recommendations based on millions spent on ads for Loan Officers and Real Estate agents.
Do You Have Google Ads?
Coming soon!

This site or service is not a part of the Facebook website or Facebook Inc. Additionally, this site is not endorsed by Facebook in any way.
Facebook is a trademark of Facebook, Inc.
We don’t believe in get-rich-quick programs. We believe in hard work, adding value and serving others. And that’s what our programs are designed to help you do. As stated by law, we can not and do not make any guarantees about your own ability to get results or earn any money with our ideas, information, programs or strategies. We don’t know you and, besides, your results in life are up to you. Agreed? We’re here to help by giving you our greatest strategies to move you forward, faster. However, nothing on this page or any of our websites or emails is a promise or guarantee of future earnings. Any financial numbers referenced here, or on any of our sites or emails, are simply estimates or projections or past results, and should not be considered exact, actual or as a promise of potential earnings – all numbers are illustrative only. If you have questions, email:
support@leadhackers.app
Copyright © 2024 | Lead Hackers | All rights reserved | Terms | Privacy | Earnings Disclaimer | Disclosures | Contact